SecArchBot: AI-powered Zero Trust architecture analysis
.webp)

Traditionally, when teams need to build new solutions or integrate two systems, applications, or services, there’s a significant risk of misconfigurations, unverified trust assumptions, and weak access controls. These gaps can expose organisations to lateral movement attacks, data breaches, and unauthorised access — especially in today’s complex, interconnected environments.
To address these risks, many organisations are turning to Zero Trust Architecture (ZTA) — a security model based on the principle of "never trust, always verify." However, analysing system architecture through a Zero Trust lens remains a complex and resource-intensive task, requiring specialised expertise that many teams lack.
That’s where SecArchBot comes in. Developed by the Deriv Security Team, SecArchBot is an innovative Slack-based tool that leverages artificial intelligence to automate Zero Trust architecture analysis. It enables teams to identify security gaps, recommend solutions, and generate secure architecture diagrams — all within Slack conversations.
What is SecArchBot?
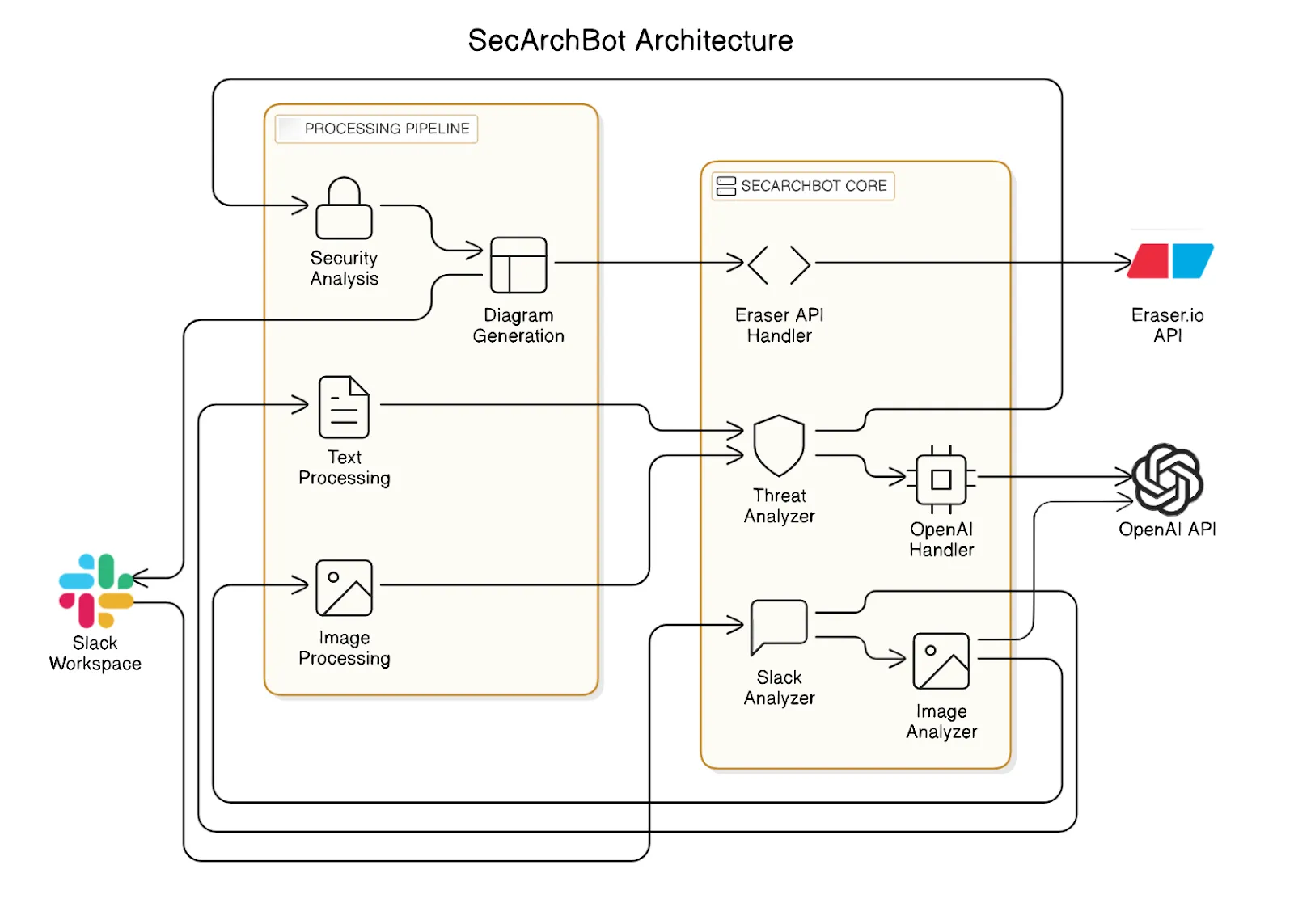
SecArchBot is a Slack bot that analyses system architecture diagrams and text descriptions through a zero trust security lens. It combines optical character recognition (OCR), advanced AI models (OpenAI GPT-4 and Google Gemini), and diagram generation capabilities to provide comprehensive security analysis and recommendations directly within Slack conversations.
How SecArchBot works
The workflow of SecArchBot is elegantly simple yet powerful:
- Problem Statement Submission: Users share their problem statements in text, or a sample architecture diagram they've built in Slack by mentioning the bot or sending direct messages.
- Text Extraction: The bot uses OCR technology (via Pytesseract) or Google's Gemini Vision API to extract text and component information from architecture diagrams.
- AI Analysis: The extracted information is analysed using OpenAI's GPT-4 with specialised prompts focused on zero trust principles.
- Security Recommendations: The bot generates detailed security recommendations, including multiple solution approaches with technical components, implementation complexity, and security posture scores.
- Visualisation: Using the Eraser.io API, the bot generates a proposed secure architecture diagram that incorporates the recommended security controls.
- Results Presentation: All findings and recommendations are formatted and presented back to the user in the Slack thread, complete with the generated secure architecture diagram.
Key technical components
Slack integration
SecArchBot uses the Slack Bolt framework to handle interactions with Slack's API. It responds to both direct mentions in channels and direct messages, making it flexible for different team workflows
# Initialise the Slack app
app = App(
token=os.environ.get("SLACK_BOT_TOKEN"),
signing_secret=os.environ.get("SLACK_SIGNING_SECRET"))
Image analysis
The bot uses multiple methods to extract information from architecture diagrams:
1. Pytesseract OCR: For basic text extraction from images
def extract_text_from_image(image_data: bytes) -> str:
# Convert bytes to PIL Image image = Image.open(io.BytesIO(image_data))
# Extract text using pytesseract text = pytesseract.image_to_string(image)
# Clean up the text cleaned_text = text.strip()
# Add some context about the text being from an architecture diagram
formatted_text = f"""Architecture Diagram Analysis:
Components and Connections Identified:{cleaned_text}
Note: This text was extracted from an architecture diagram using OCR. The structure and layout of components may provide additional context beyond the extracted text."""
return formatted_text2. Google Gemini vision API: For more advanced image understanding
def extract_text_from_image_gemini(image_data: bytes) -> str:
# Detect image format using PIL
image = Image.open(io.BytesIO(image_data))
mime_type = Image.MIME[image.format]
client = genai.Client(api_key=GEMINI_API_KEY)
response = client.models.generate_content(
model="gemini-2.0-flash-exp",
contents=[
"What is this image?",
image
])
gemini_analysis = response.text
return formatted_textAI-powered analysis
SecArchBot leverages OpenAI's GPT-4 model to analyse architecture diagrams through a zero trust lens. The analysis uses two specialised prompts:
1. Zero Trust architecture analysis prompt:
def create_image_analysis_prompt():
"""Create prompt for zero trust architecture analysis"""
return """
You are a Senior Security Architect specialising in zero trust architecture. Analyse the following system architecture diagram through a zero trust lens, focusing on the principle of "never trust, always verify" and providing recommendations for implementing zero trust controls.
Analyse the following aspects:
1. Identity and Access:
- Authentication mechanisms and their placement
- Identity providers and federation
- Device authentication and attestation
- Session management and continuous verification
2. Network Architecture:
- Micro-segmentation implementation
- Service mesh controls
- Network isolation and boundaries
- Access proxy placement
- Traffic inspection points
3. Data Protection:
- Encryption points (in-transit and at-rest)
- Key management infrastructure
- Data access controls
- Secrets management
4. Zero Trust Controls:
- Policy enforcement points
- Trust boundaries and transitions
- Authorisation checkpoints
- Monitoring and logging points
5. Security Gaps:
- Missing identity verification points
- Insufficient access controls
- Unprotected data flows
- Lack of micro-segmentation
- Missing authentication/authorisation checks
Provide a structured analysis focusing on:
1. Current zero trust readiness
2. Major security gaps from a zero trust perspective
3. Specific recommendations for implementing zero trust controls
4. Priority areas for enhancement
IMPORTANT:
- Focus on concrete, technical details visible in the diagram
- Identify specific points where zero trust controls should be implemented
- Provide actionable recommendations for each gap identified
- Consider the end-to-end request flow and verify points
"""
2. Security architecture analysis prompt:
def create_analysis_prompt(system_name: str, service_details: str, previous_security_reports: str, app_input: str) -> str:
return f"""
Act as a Senior Security Architect analysing security architecture patterns and their implications. Your task is to:
1. First, understand the current security architecture:
- What security boundaries exist? - How is trust established and verified?
- What security properties are being maintained?2.
Then analyse proposed architectural changes:
- How do they affect existing security boundaries?
- What security properties are preserved or modified?
- What trust assumptions are being made?3. Consider the security model:
- How is the trust model affected? - What security invariants must be maintained?
- What security properties could be compromised?
...
"""
The analysis is structured to provide multiple solution approaches with detailed technical components, implementation complexity, and security posture scores.
Diagram generation
After analysis, SecArchBot uses the Eraser.io API to generate a proposed secure architecture diagram based on the recommended solution:
# Generate the diagram
diagram_prompt = f"""
Generate a detailed zero trust architecture diagram for the recommended solution:
System: {combined_text}
Approach: {solution_details['approach']}
Key Components to Visualise:
1. Identity & Authentication:
{chr(10).join(f'- {item}' for item in solution_details['technical_components']['identity_provider'])}
2. Network Security:
{chr(10).join(f'- {item}' for item in solution_details['technical_components']['network_architecture'])}
3. Security Rationale:
{solution_details['technical_components']['security_rationale']}
Required Elements:
1. Authentication & Authorisation Flow
2. Network Segmentation Boundaries
3. Data Encryption Points
4. Security Control Checkpoints
5. Trust Boundaries
"""
diagram_response = eraser.generate_diagram_from_prompt(diagram_prompt)Zero Trust analysis focus
The bot's analysis is specifically tailored to zero trust principles, focusing on:
- Identity and Access: Authentication mechanisms, identity providers, device authentication, and session management.
- Network Architecture: Micro-segmentation, service mesh controls, network isolation, and traffic inspection.
- Data Protection: Encryption points, key management, data access controls, and secrets management.
- Zero Trust Controls: Policy enforcement points, trust boundaries, authorization checkpoints, and monitoring.
- Security Gaps: Missing identity verification, insufficient access controls, unprotected data flows, and lack of micro-segmentation.
Output format
SecArchBot provides its analysis in a structured format that includes:
- Multiple Solution Approaches: Each with:
- A descriptive name and approach summary
- Technical components (identity providers and network architecture)
- Security rationale explaining why the approach maintains or impacts security boundaries
- Implementation complexity (High/Medium/Low)
- Security posture score
- Final Recommendation: Including:
- Selected solution from the proposed approaches
- Technical reasons for the selection
- Implementation steps
- Secure Architecture Diagram: A visual representation of the recommended solution generated by Eraser.io.
Benefits for security teams
SecArchBot offers several key benefits for security teams:
- Democratised Expertise: Provides zero trust architecture expertise to teams that may not have dedicated security architects.
- Rapid Analysis: Delivers comprehensive security analysis in minutes rather than days or weeks.
- Visual Recommendations: Generates visual secure architecture diagrams that are easier to understand and implement.
- Collaboration: Integrates directly with Slack, enabling seamless collaboration among team members.
- Multiple Solutions: Offers multiple security approaches with different complexity levels, allowing teams to choose based on their constraints.
Implementation requirements
To deploy SecArchBot, you'll need:
- A Slack workspace with admin privileges
- API keys for:
- OpenAI
- Google Gemini
- Eraser.io for diagram generation
- Slack bot token, app token, and signing secret
- Python environment with the required dependencies:
- slack-bolt
- requests
- python-dotenv
- openai
- pytesseract
- Pillow
- google-genai
Docker support
SecArchBot can be easily deployed using Docker:
docker build -t secarchbot .
docker run -d --env-file .env secarchbotOr using Docker Compose:
docker-compose up -dExample usage
Users can interact with SecArchBot by:
- Sending a direct message to the bot
- Mentioning @SecArchBot in a channel
Example query:
@SecArchBot The payment automation team wants to set up an SFTP server for our main bank through which they can download payment instructions. The idea is to use cloudflare and an SFTP docker container on the existing payroll server.
Conclusion
In our quest to build the optimal AI agent, we evaluated several leading models. While DeepSeek R1 showed initial promise, its API's inconsistent uptime presented a significant hurdle during our initial deployment. Similarly, Qwen, though powerful, didn't quite align with the specific output style we envisioned. Ultimately, OpenAI's robust and reliable platform, coupled with its superior output quality for architecture analysis, proved to be the ideal foundation for our project. Additionally, we incorporated Gemini Flash, leveraging its cost-effectiveness and exceptional image analysis capabilities for specific visual processing tasks within our agent's workflow.
SecArchBot represents an innovative approach to security architecture analysis, bringing AI-powered zero trust expertise directly into team collaboration platforms. Built using advanced AI coding tools and techniques, SecArchBot leverages cutting-edge machine-learning techniques to automate and enhance security assessments. By combining OCR, advanced AI models, and diagram generation capabilities, it provides comprehensive security recommendations that would traditionally require specialised expertise.
During its development, experimentation with various AI models, including Qwen, played a crucial role in refining its accuracy and effectiveness. By testing different models and approaches, the team ensured that SecArchBot delivers the most precise and actionable security insights possible.
As organisations continue to adopt zero trust principles, tools like SecArchBot will play an increasingly important role in democratising security expertise and ensuring that all systems are designed with security in mind from the ground up.
Source Code & Contributions: https://github.com/deriv-com/security-tools/tree/master/security_architect_bot





























%2520(1).png)
.webp)
.jpeg)



%2520(1).webp)
.webp)



.webp)
.webp)












.webp)





